Google Workspace
Overview
ShiftControl supports both user sync and Single Sign-On (SSO) for Google Workspace. Since Google Workspace is a core application in many organizations and has its own directory of users, it is treated a bit differently than regular SSO apps.
Google Workspace user synchronization is handled through a dedicated Google App via JumpCloud. However, once we enforce SSO, your users will need to be assigned the SSO application in order to log into Google Workspace and related services.
Supported Licenses
Google Workspace supports SSO on all licenses!
What you need to know
Add a Google Application and Configure SSO
Follow these instructions in order to add Google Workspace to ShiftControl and configure Single Sign-on (SSO).
We recommend configuring SSO for your entire organization and excluding any Organization Units (OUs) as required. Please see the "Google does not enforce SSO for Admins" in the previous section for more info on why we recommend this.
Create an OU to test authentication
Log in to the Google Workspace Admin Panel
Go to https://admin.google.com, log in as an Admin.
Manage OUs
Go to Directory→Organizational Units
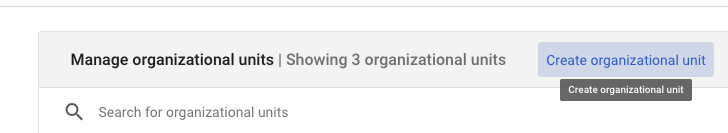
Create an OU
Click on Create organizational unit.
Create an OU
Set the name as SSO-Test, give it a description, and add it to your parent organization
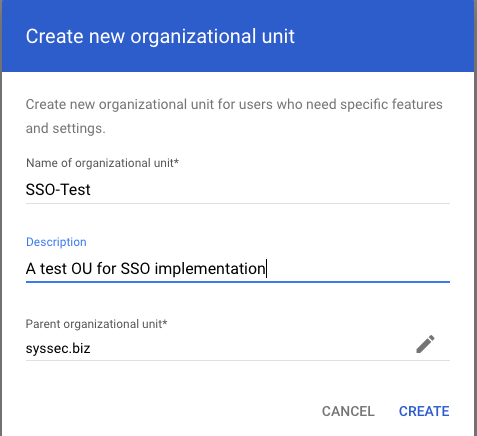
You've not created an Organization Unit that we can use to assign our SSO configuration. We'll use this to ensure we can test it before you deploy it for all users.
(Optional) Configure a SAML Profile to configure SSO
Go to SSO with third-party IdP
Go to Security→Authentication→SSO with third party IdP
Add SAML profile
We’ll add a profile first so we can test SSO for a specific OU, click on ADD SAML PROFILE
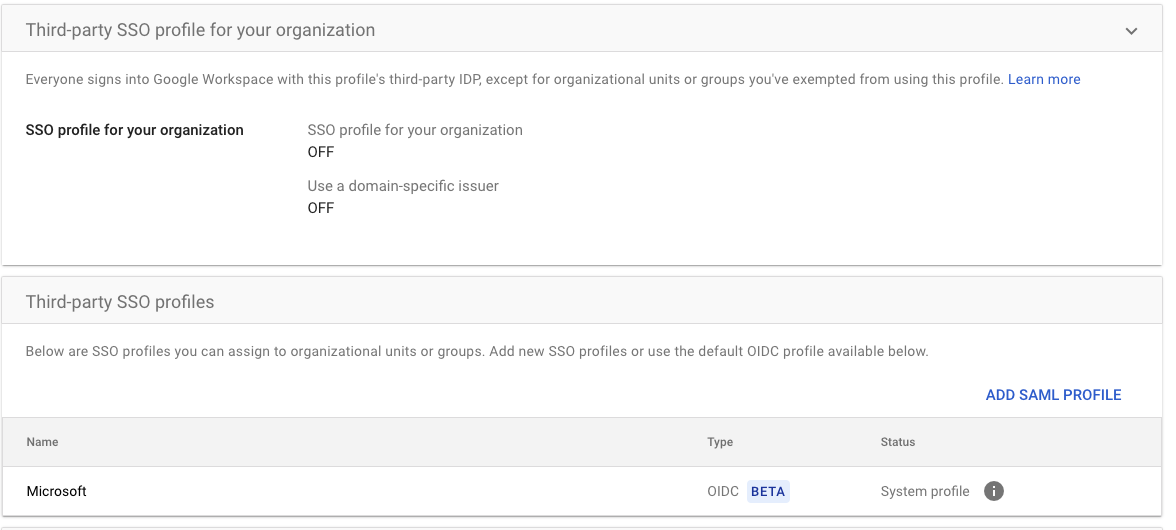
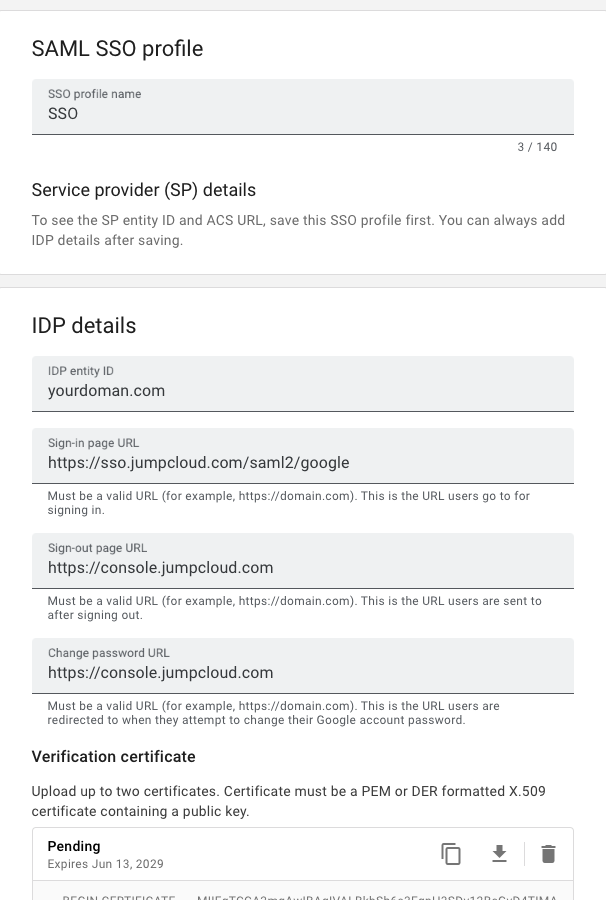
Configure the SAML profile
Configure the SAML profile:
- SSO profile name: SSO or any other unique name
- IDP Entity ID: yourdomain.com
- Sign-in Page URL: The “IDP URL” from the app’s SSO page in JumpCloud (Soon to be shown in ShiftControl)
- Sign-out page URL: https://console.jumpcloud.com
- Change password URL: https://console.jumpcloud.com
- Upload the certificate: Found by clicking Download certificate on the left in the app’s SSO page in JumpCloud (Soon to be available in ShiftControl)
Save the profile
Click Save
Review the configuration page
You’ll come to a page that shows the configuration, we’ll need the Entity ID and ACS URL.
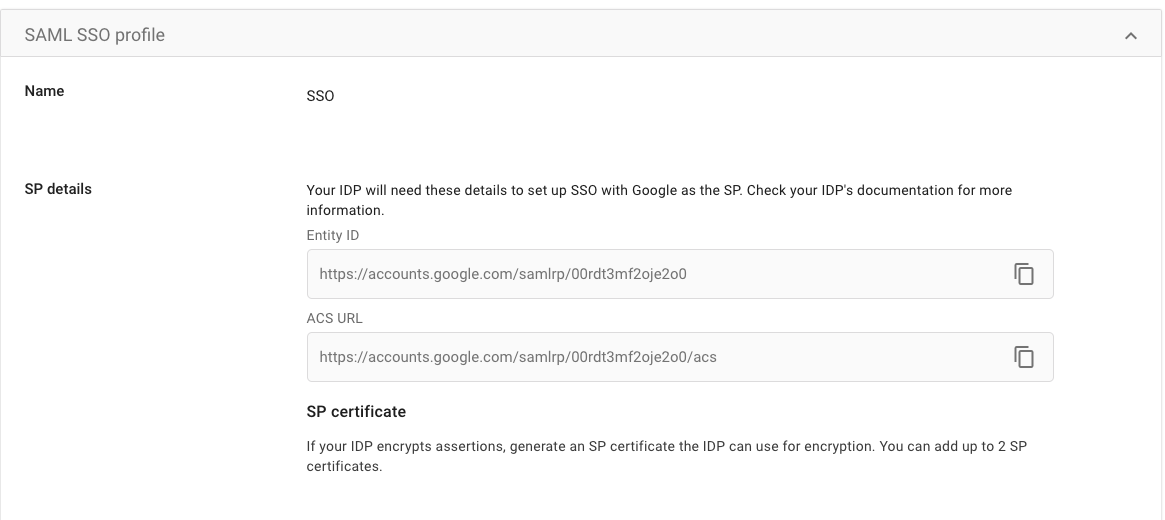
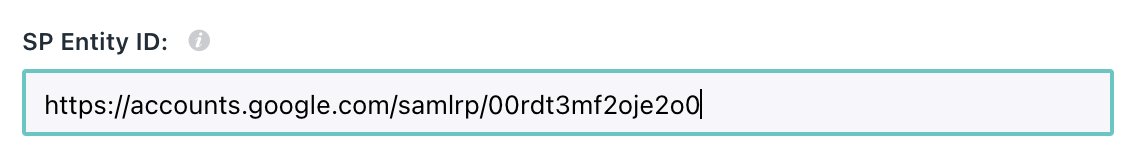
Copy the SP Entity ID
Copy the Entity ID and paste it into JumpCloud’s App in the SSO area (Coming soon to the ShiftControl UI):
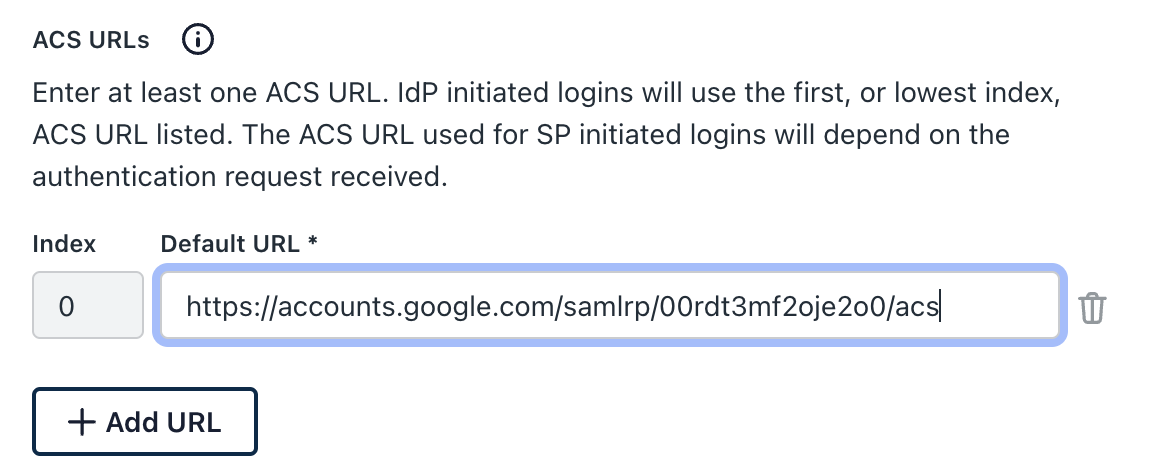
Copy the ACS Url
Copy the ACS URL and paste it into JumpCloud’s App in the SSO area (Coming soon to the ShiftControl UI):
Save
Click Save in JumpCloud and Click Back in Google Workspace. We’re now ready to assign the profile to your OU.
Assign a SAML Profile to an Organizational Unit (OU)
Go to SSO with third-party IdP
Go to Security→Authentication→SSO with third party IdP
Click on Get Started
Click on Get Started (if you haven’t assigned any profiles in the past)
Select SSO-Test in Organizational Unit area
Click on SSO-Test on the left in the Organizational Unit area
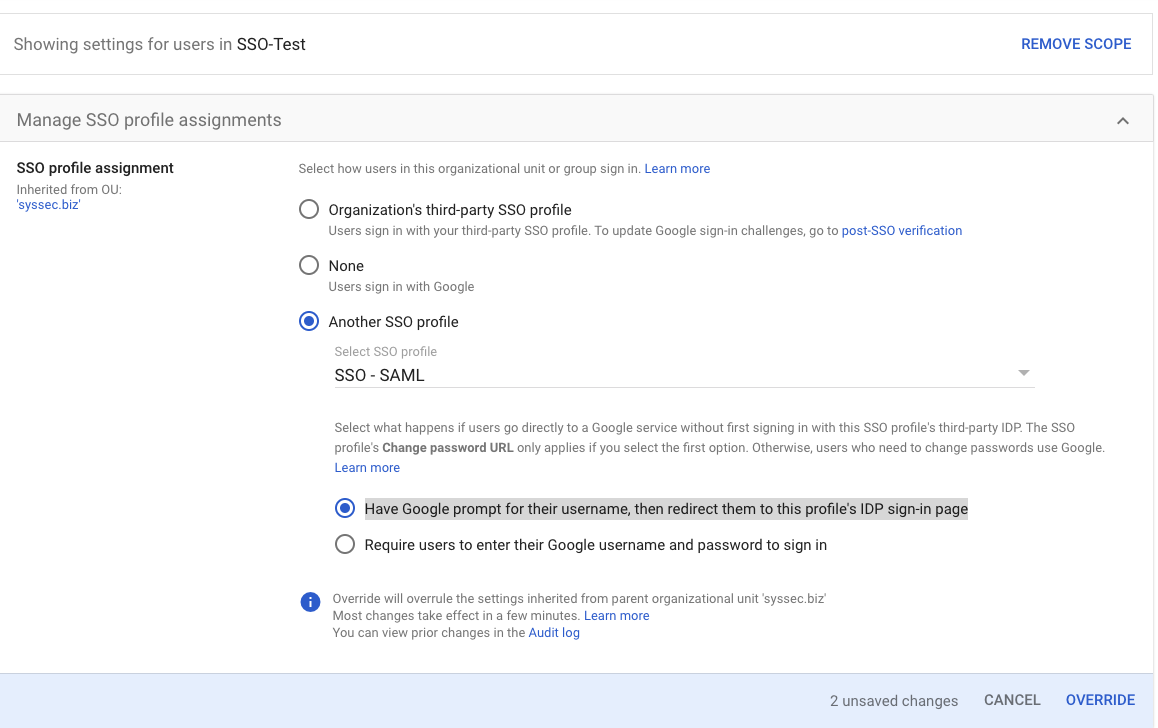
Choose Another SSO Profile
Choose Another SSO Profile, and select your SSO-SAML profile we built before.
Set Google prompt for username
Keep the default of “Have Google prompt for their username, then redirect them to this profile's IDP sign-in page”
Click Override
Then click Override
Assign a user into the OU for testing
You are now ready to assign a user into that OU for testing.
Assign a user into the SSO Testing Organizational Unit
Go to the users directory
Go to Directory→Users
Select the user from the list
Select the user from the list
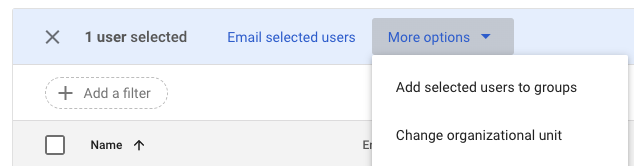
Change organizational unit
Click on Change organizational unit in the More options menu
Select SSO-Test and click Continue
Select SSO-Test and click Continue
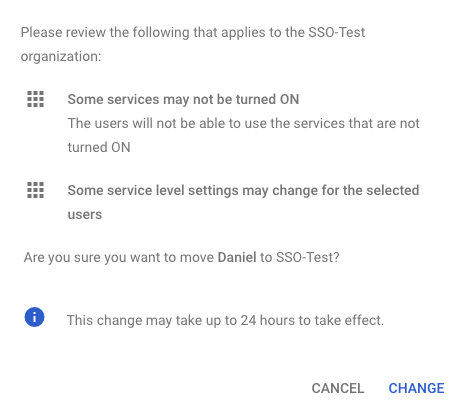
Review the warning and click Change
Review the warning and click Change, there will be no impact other than SSO if you don’t currently use OUs as all other rules are inherited from the main organization.
Verify user in SSO Test OU
The user is now in the SSO Test OU.
From here, you can open an incognito window and try authenticating to google.com. Make sure the user you are using to test with is assigned the Application in the ShiftControl admin panel.